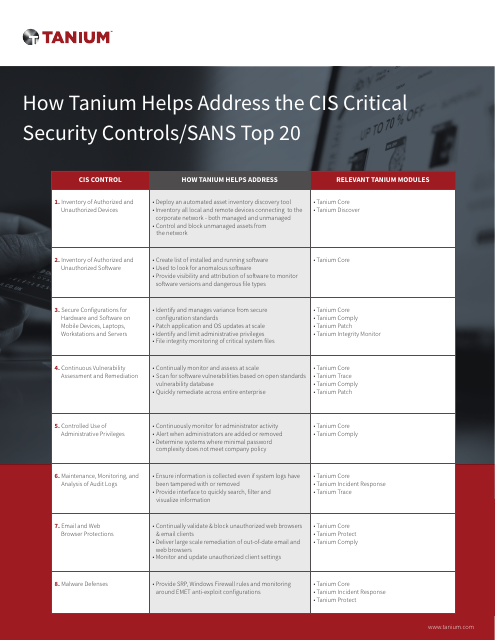
How Tanium helps address the CIS Critical Security Controls/SANS Top 20 | Cyentia Cybersecurity Research Library

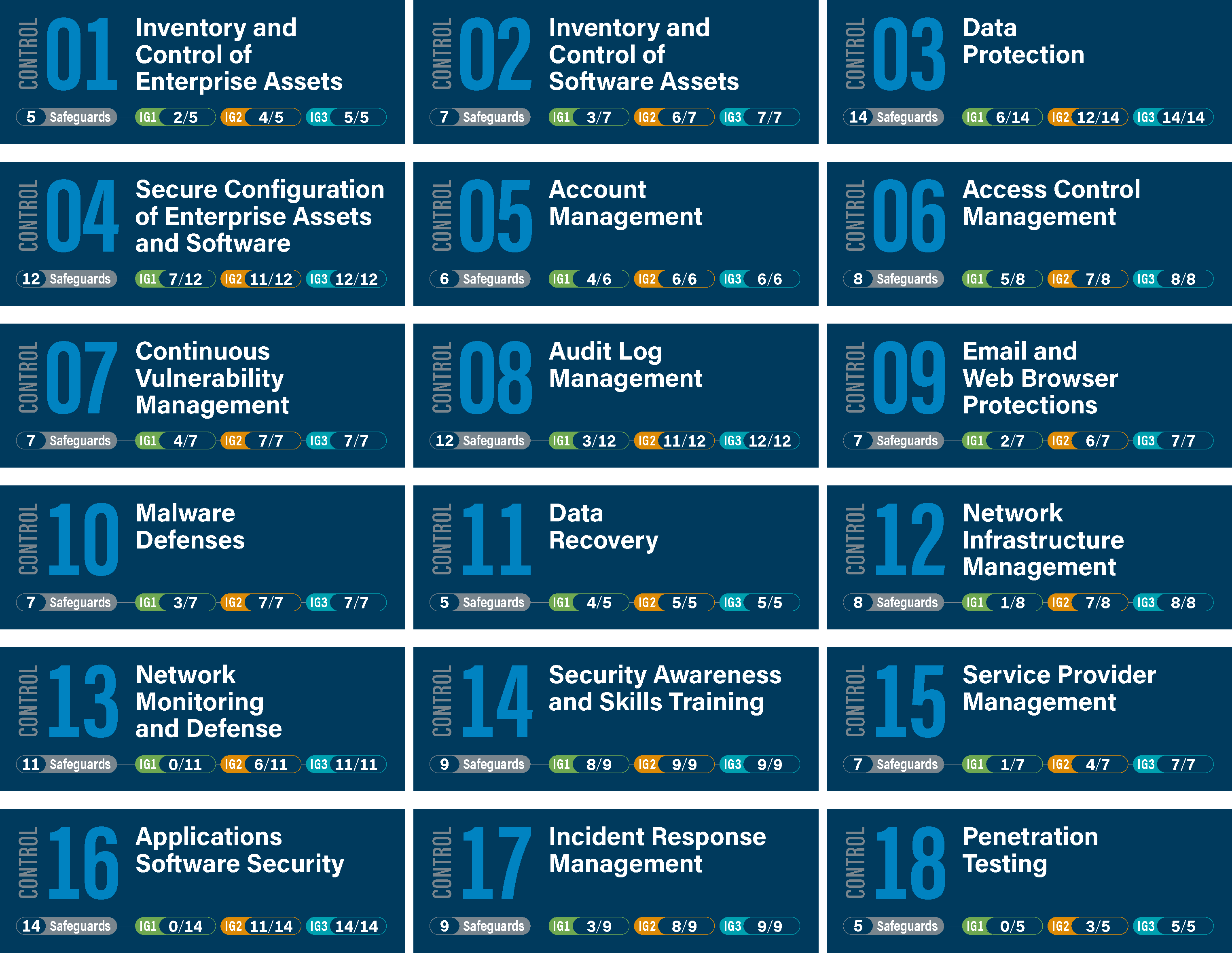
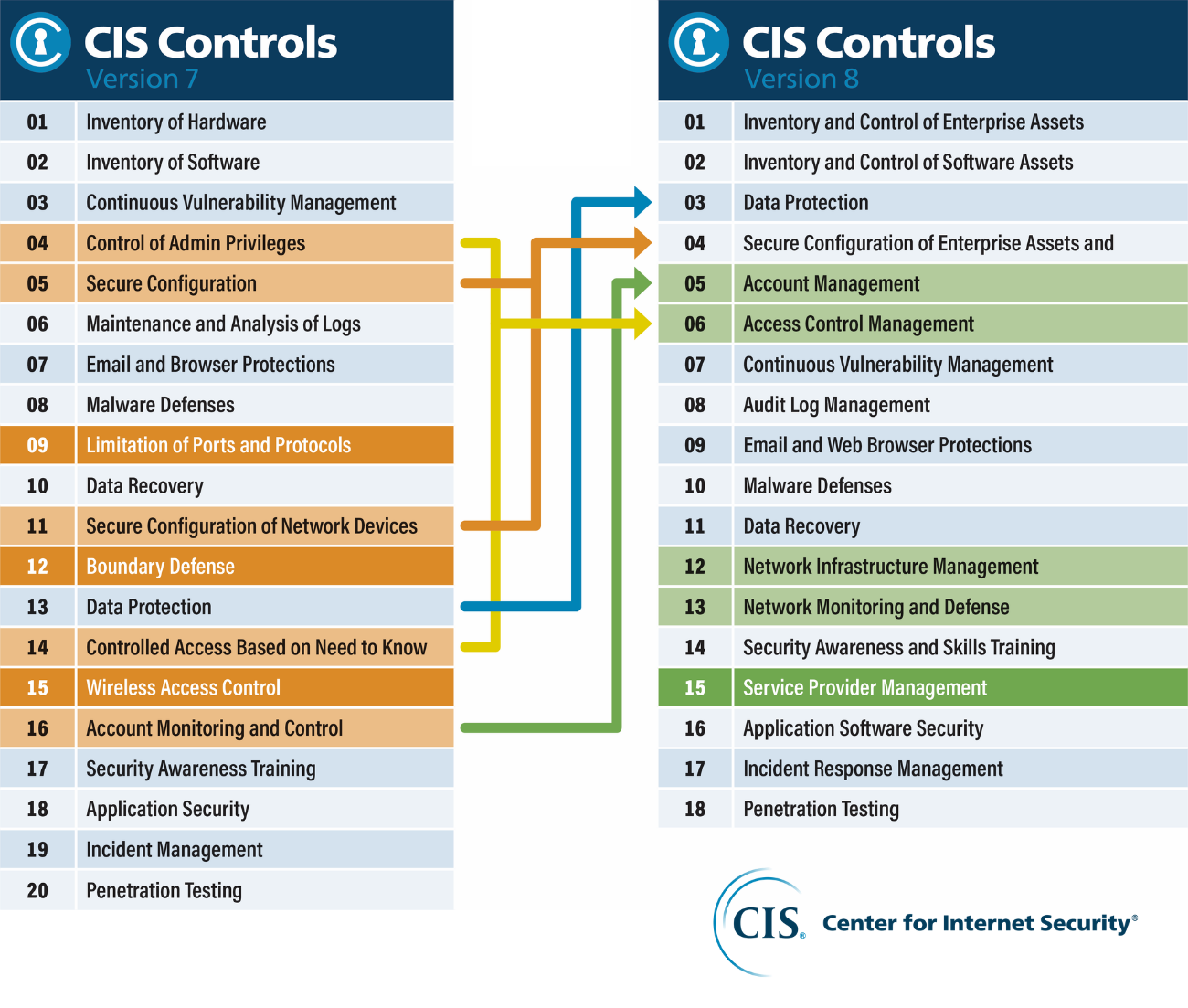
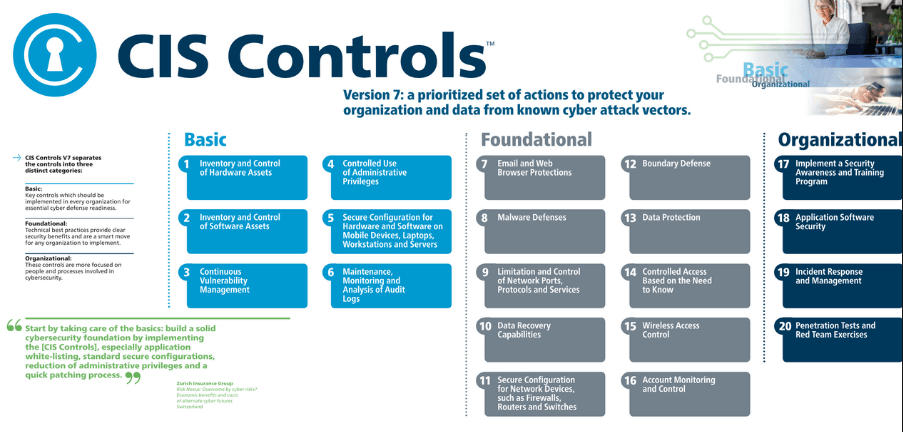
Michael Fisher on X: "What are the top 20 controls for a healthy network # Security posture? {Infographic} #CyberSecurity #infosec #education #DevOps #Malware #databreach #Pentesting #IRP https://t.co/M6bSaA0361" / X

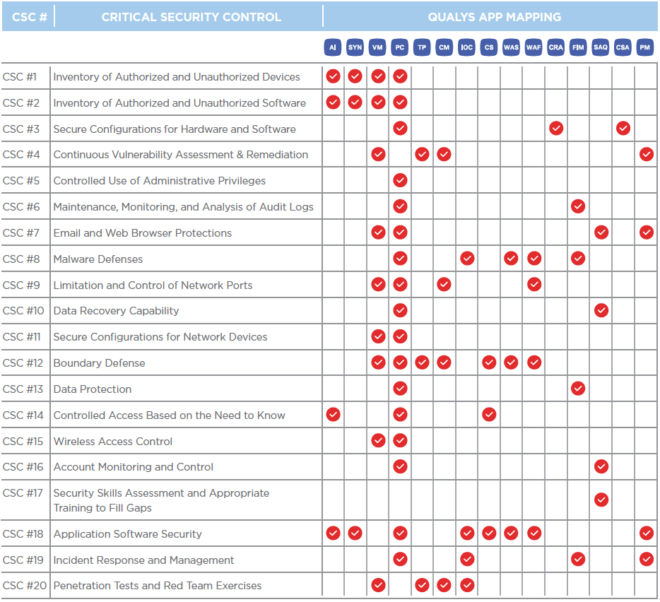
At least 3 of SANS top 20 Critical Controls require addressing SSH key based access & SSH key management to know who can access what & enforce boundary.

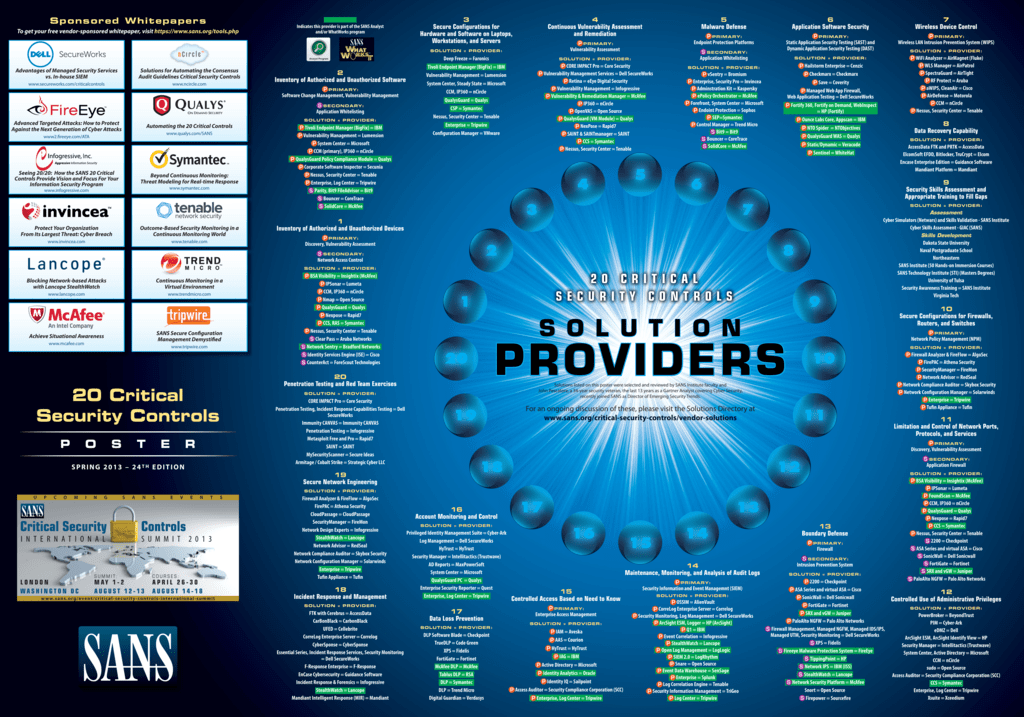
Complementing a Security Management Model with the 20 Critical Security Controls: Academic Paper | SecurityOrb.com